Still using a traditional VPN? Unfortunately, so are attackers. IPsec and SSL VPNs have served their purposes over the years, but they were built for a time when security meant protecting a network perimeter. That perimeter no longer exists.
Our people, data, and devices are everywhere now, and so our security must follow them. If security doesn’t keep pace, performance, protection, and manageability will inevitably suffer.
Enter Secure Service Edge, or SSE. The answer this time isn’t another patch or upgrade, rather a new approach entirely. SSE is a modern, cloud-delivered approach that’s built for today’s remote, hybrid, and cloud-first environments. It secures remote access with a Zero Trust model — protecting users, data, and applications wherever they are without the complexity or risk of traditional tunnels.
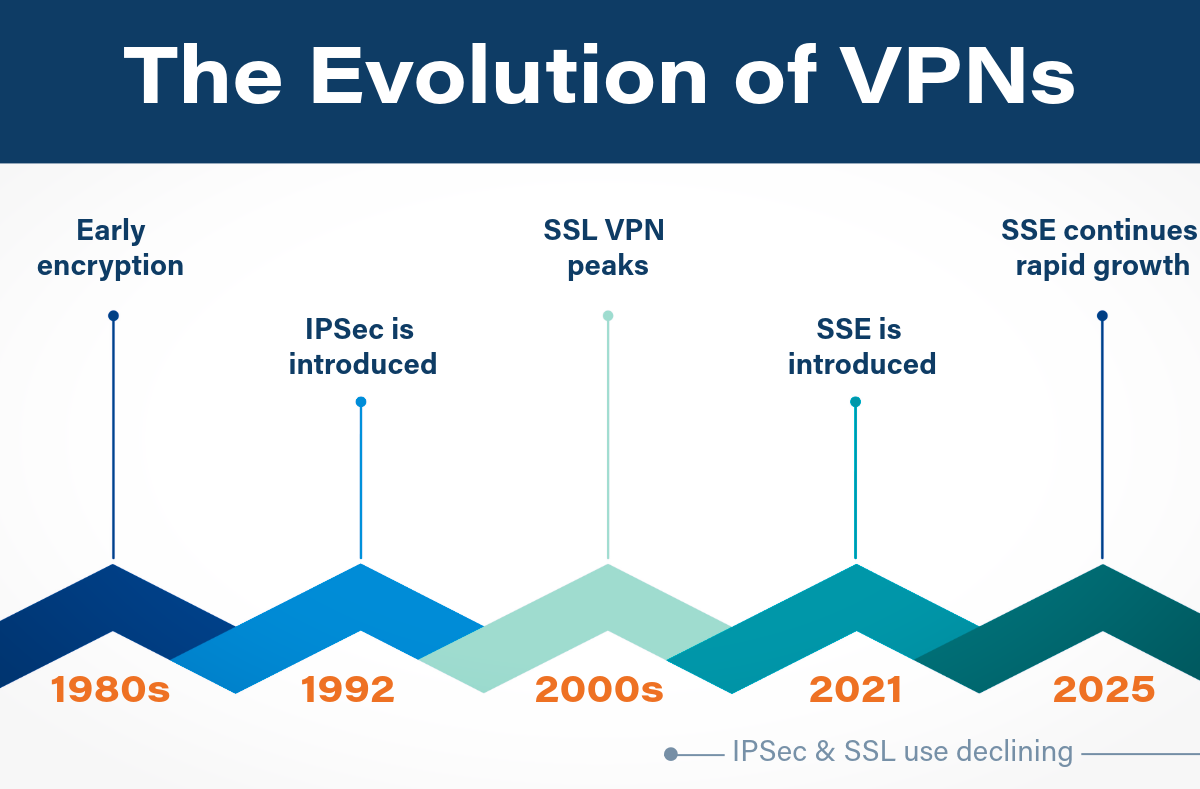
VPNs Then and Now: The Shift Toward Secure Service Edge and Zero Trust
As digital ecosystems expand and threats evolve, remote access has shifted from a network-centric utility to a foundational element of cybersecurity strategy. This shift is reflected in the steady decline of legacy VPN technologies like IPsec and SSL, and the growing adoption of Secure Service Edge (SSE) — a modern, cloud-native approach aligned with Zero Trust principles.
- 1990s: IPsec VPN – Built for on-premises access; gave full tunnel into the corporate network
- 2000s: SSL VPN – Easier web-based access to specific apps, but still used tunneling
- 2020s: SSE – Cloud-native, context-aware, built for Zero Trust and SaaS environments
VPN Vulnerabilities in 2024: Key Risks and Data from Zscaler
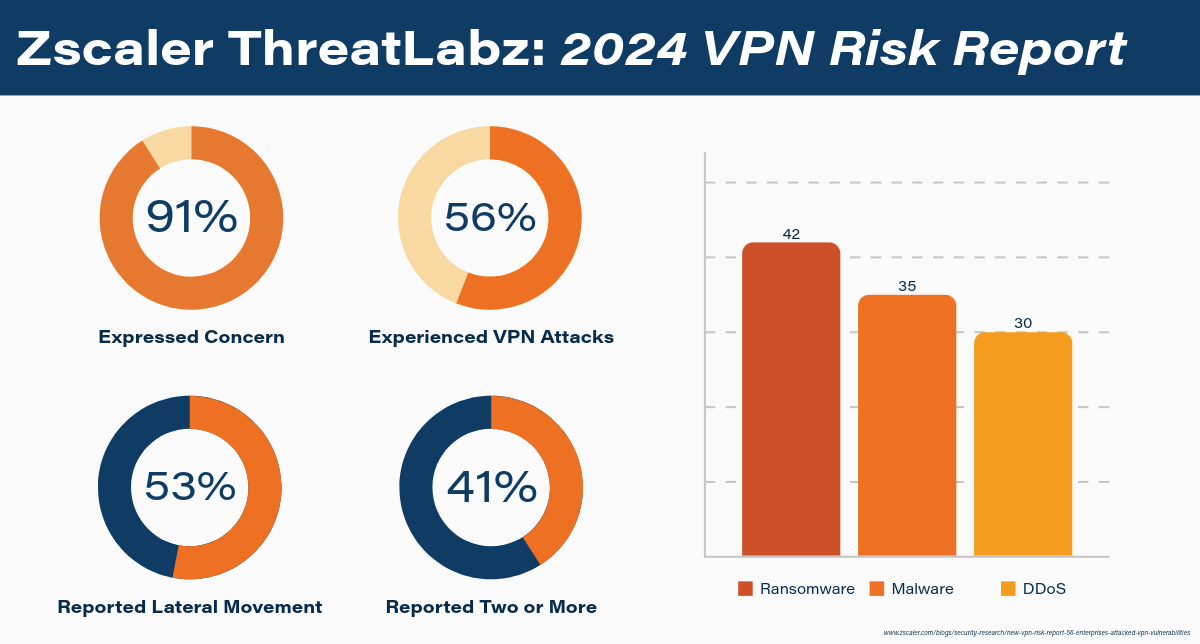
If you’re feeling the strain of managing remote access with aging VPN tools, you’re not alone — and the data backs it up. Recent findings from the Zscaler ThreatLabz 2024 VPN Risk Report reveal just how widespread and persistent VPN-related vulnerabilities have become. As organizations continue to rely on legacy remote access tools, attackers are taking advantage of the gaps — leading to repeated breaches, lateral movement, and rising concerns among IT and security leaders. Here’s a snapshot of what today’s VPN landscape really looks like:
- Prevalence of Attacks: 56% of organizations experienced VPN-related cyberattacks in the past year.
- Multiple Incidents: 41% of those affected faced two or more VPN-related attacks, showing that VPN vulnerabilities often lead to repeated exploitation.
- Common Threats: The top attack types exploiting VPNs were ransomware (42%), malware (35%), and DDoS attacks (30%).
- Lateral Movement: 53% of enterprises breached via VPNs reported lateral movement, allowing attackers to spread inside the network and escalate access.
- Widespread Concern: A staggering 91% of IT leaders expressed concerns that VPNs could compromise their organization’s security posture.
Why Legacy VPNs Fail: Security, Performance & Operational Risks
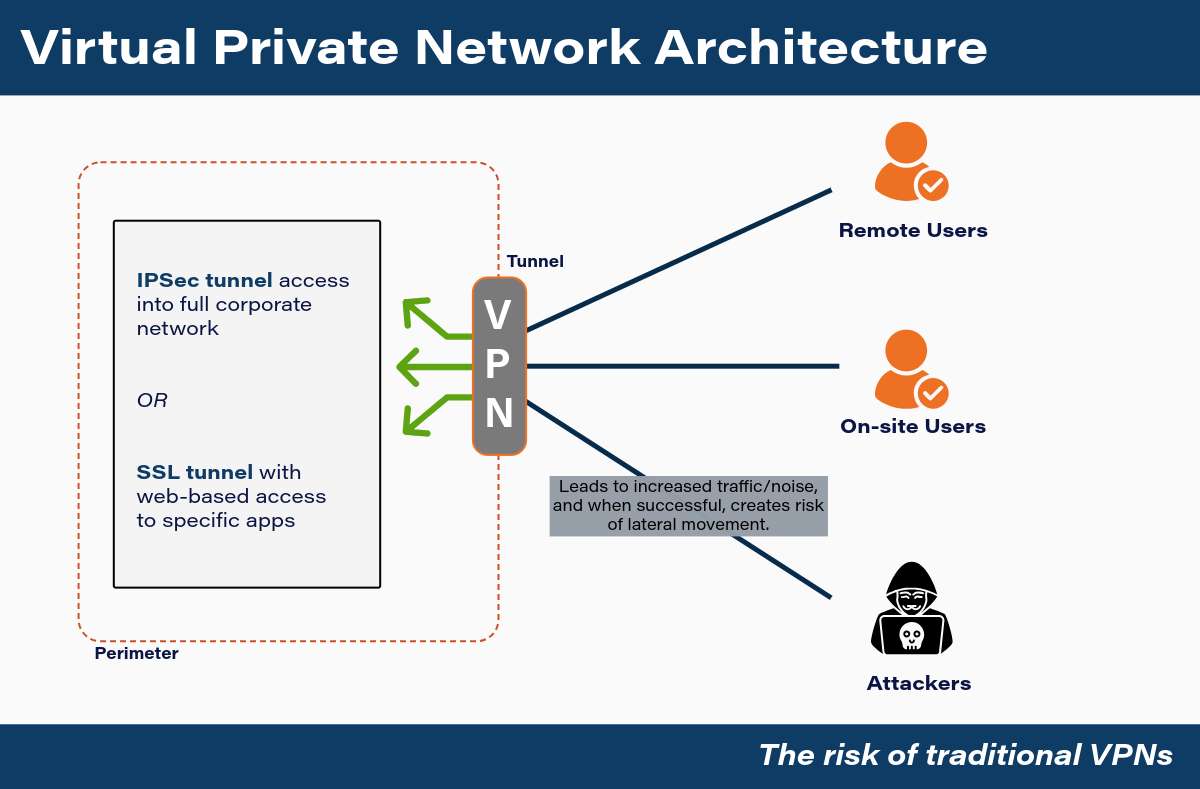
So, what’s the deal? Why are traditional VPNs a challenge to maintain in today’s evolving world?
- Security Concerns
- Credentials are a significant target in breaches
- Lateral movement risk once inside the network (once they’re in, they won’t stop)
- Increasing ransomware, phishing, and credential-stuffing attacks
- Operational Challenges
- Constant management of access rules, patching, troubleshooting
- Legacy infrastructure strains under growing remote access demand
- Increased attack attempts = more traffic and noise to your IT team
- Performance Bottlenecks
- Backhauling traffic to the data center slows access to cloud apps
- Poor user experiences = reduced productivity
What Is Secure Service Edge (SSE)? A Modern VPN Alternative Explained
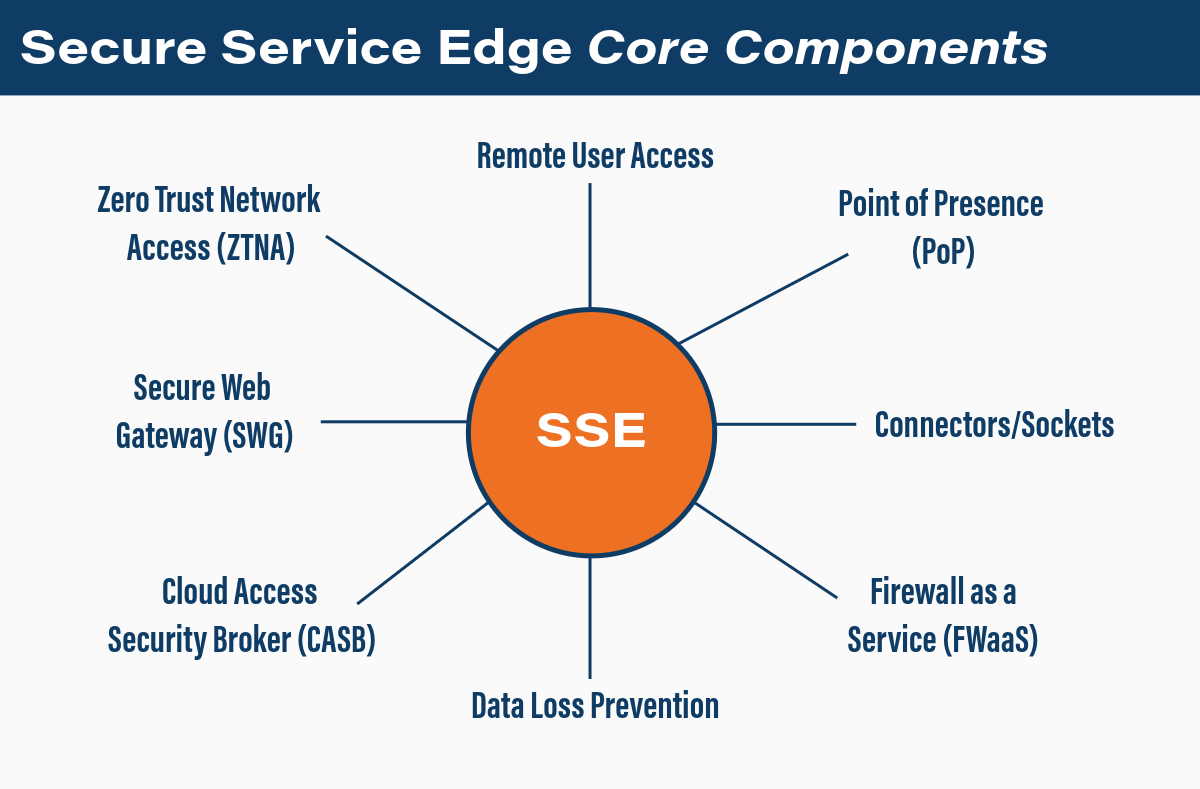
Defined simply, SSE is a cloud-delivered security framework that includes:
- Remote User Access:
- Replaces traditional VPNs with agent-based or agentless, session-based access to corporate resources. Enables deep traffic inspection and secure third-party access without requiring a client.
- Secure Web Gateway (SWG):
- Controls and restricts user access to websites based on categories, URLs, keywords, or risk levels to prevent exposure to malicious or non-compliant content
- Zero Trust Network Access (ZTNA):
- Grants access based on identity and context, ensuring users only reach resources they’re authorized for—minimizing lateral movement and risk.
- Cloud Access Security Broker (CASB):
- Monitors and governs access to cloud applications, balancing productivity with security and compliance enforcement.
- Data Loss Prevention:
- Detects and blocks unauthorized sharing or exfiltration of sensitive data, including encrypted traffic inspection.
- Connectors/Sockets:
- Lightweight on-prem appliances that initiate outbound sessions to the SSE Point of Presence (PoP), acting as secure gateways for branch offices or data centers.
- Point of Presence (PoP):
- A globally distributed network of access nodes that deliver low-latency, secure connectivity to SSE services—bringing security closer to the user.
- Firewall as a Service (FWaaS):
- Cloud-based firewall protection as part of a Security Service Edge (SSE) solution to secure traffic.
SSE provides more security for all, less management for IT teams, and enhanced user experiences by replacing outdated legacy tools with a solution that’s adapting to where and how users work.
From VPN to Zero Trust: A Step-by-Step to Modernizing Your Network Security
Changes and transitions take time, but you’re not alone. There are resources and help available to guide your next steps should you choose to take them.
Start with a risk assessment. Review your current logs and note who’s connecting, when, and why. Identify any high risk or over-permissioned access.
Once ready, test a Zero Trust Network Access (ZTNA) pilot with one team or application first. Witness the benefits in action and address any questions that arise or details you may have missed.
Finally, segment and prioritize access. You don’t have to do this overnight. Start by removing blanket network access and move toward an application-level control. You can work with security partners to avoid a rip-and-replace approach and instead explore options for temporarily running your old VPN and your new SSE side-by-side as you transition.
What Now?
Of course, you have the choice — but know that staying on VPN is a risky one. Your team has the power to modernize your organization’s security without waiting for a breach to force your hand. Weigh the costs and determine what’s best for your organization.
If you’re ready to begin your transition or want to understand your options, our team is here to guide you. Reach out to us anytime; our team will be more than happy to help.
Get In Touch (Global)
Global contact us form
"*" indicates required fields

