Technology use in our lives has evolved dramatically — we’re more capable, more connected, and more reliant on digital systems woven into our daily routines. With that growth in complexity, it only makes sense that our data backup strategies evolve as well.
What Is Data Backup and Why Is It Important?
Data backup is the process of copying and storing your information from a primary source (like a computer, server, or cloud application) onto a secondary source (such as an external drive, cloud storage, or another server) for the sake of security. It’s crucial for protecting valuable and sensitive information by allowing your data to be restored if for any reason it becomes lost, corrupted, or compromised by:
- Cyberattacks
- Hardware Failure
- Human Error
- Natural Disasters
- Software Glitches
Having an appropriate data backup strategy for your business’s needs, and implementing it diligently, doesn’t just save your data. It also saves:
- Time: Fast data recovery minimizes downtime and disruption.
- Money: Avoid costly recovery services, revenue loss, and potential legal fines or ransomware payments.
- Stress: Reduces pressure across your teams during a crisis.
- Reputation: Shows professionalism and keeps credibility with clients, partners, and the public intact.
- Data Integrity: Supports reliable analytics and sound decision-making.
- Legal & Regulatory Compliance: Helps meet regulatory standards and reduces any risk of legal action.
- Business Continuity: Key operations stay running and your customers’ services stable during disruptions.
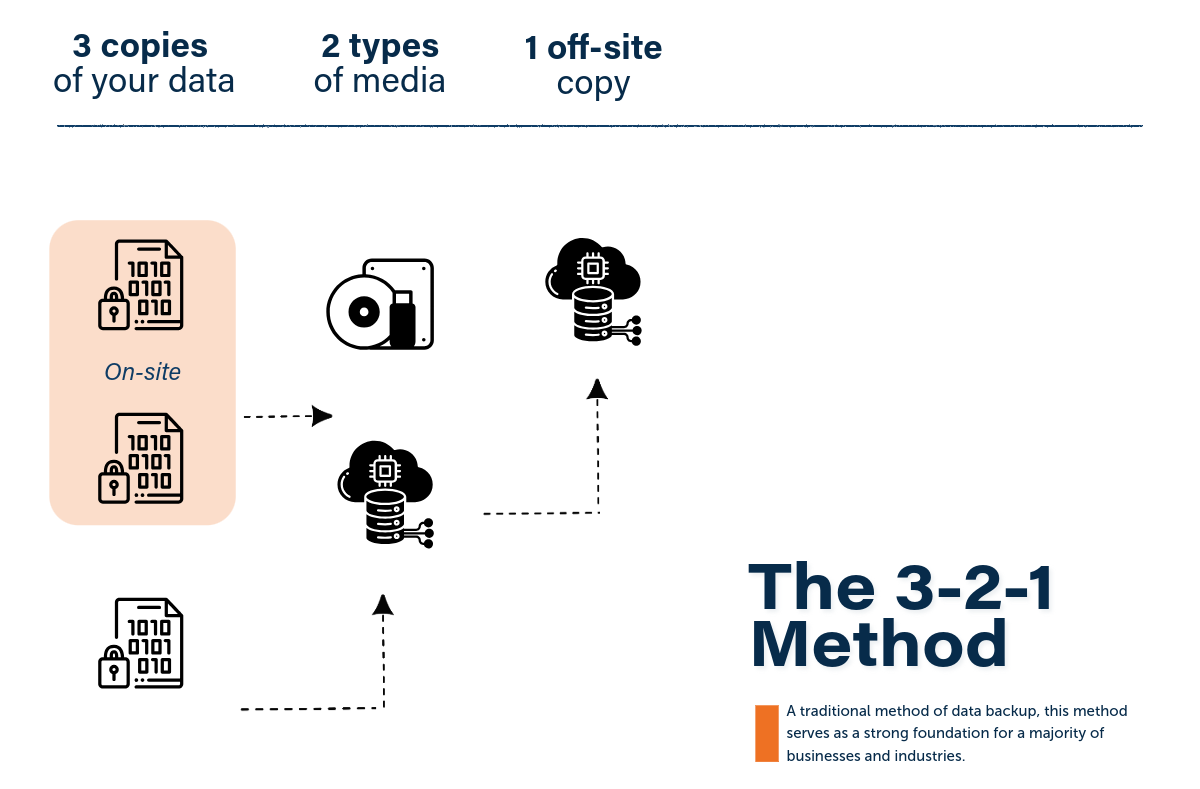
Does the 3-2-1 Rule Still Hold Value?
The 3-2-1 method is a classic data backup strategy: keep three copies of your data on two types of storage, with one off-site.
It’s long served as a foundational guideline and ultimately emphasizes the importance of data redundancy, always maintaining multiple copies, so that you’re protected, compliant, and resilient.
While that much has not changed, the rule itself has grown outdated in its lack of consideration for modern cyberthreats — like ransomware, insider attacks, and even human error.
Considering these are increasingly important for companies vulnerable to cyber-attacks, who have compliance requirements, or who have high data protection needs.
Though the 3-2-1 strategy is still valuable at its core and is better than nothing at all, we recommend selecting a data backup strategy that also guarantees immutability (backups that can’t be altered), an air gap between storage sites (physical distance/isolated backups), and regular recovery testing.
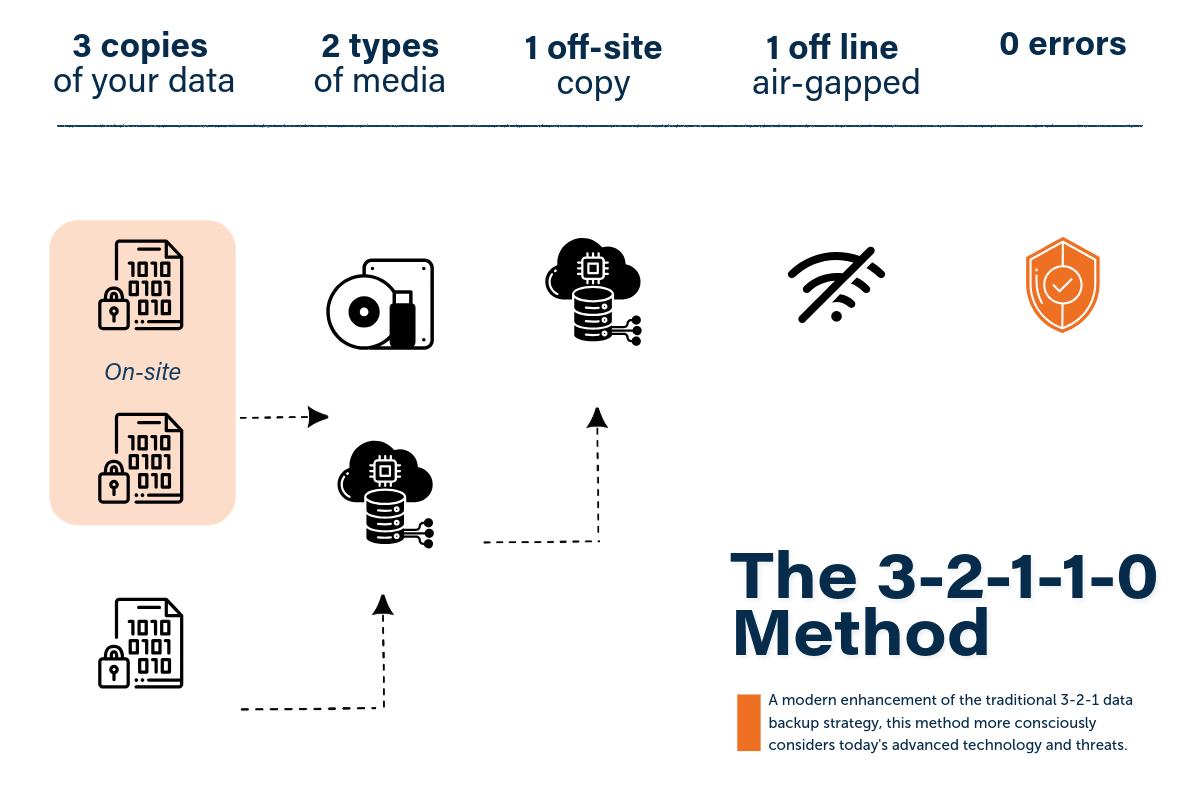
A Modern Enhancement: The 3-2-1-1-0 Rule
Enter the 3-2-1-1-0 rule. This modern enhancement to data backup takes into account vulnerabilities introduced as we become more connected. The 3-2-1-1-0 rule still requires maintaining three copies of your data on at least two different types of storage media with one of those being off-site. The addition is that you now want to be intentional in:
- Keeping one of those copies entirely offline or air gapped. Without this, a single attack could wipe out all your backups.
- Ensuring there are zero errors in recoverability—achieved by ongoing monitoring, testing, and maintenance.
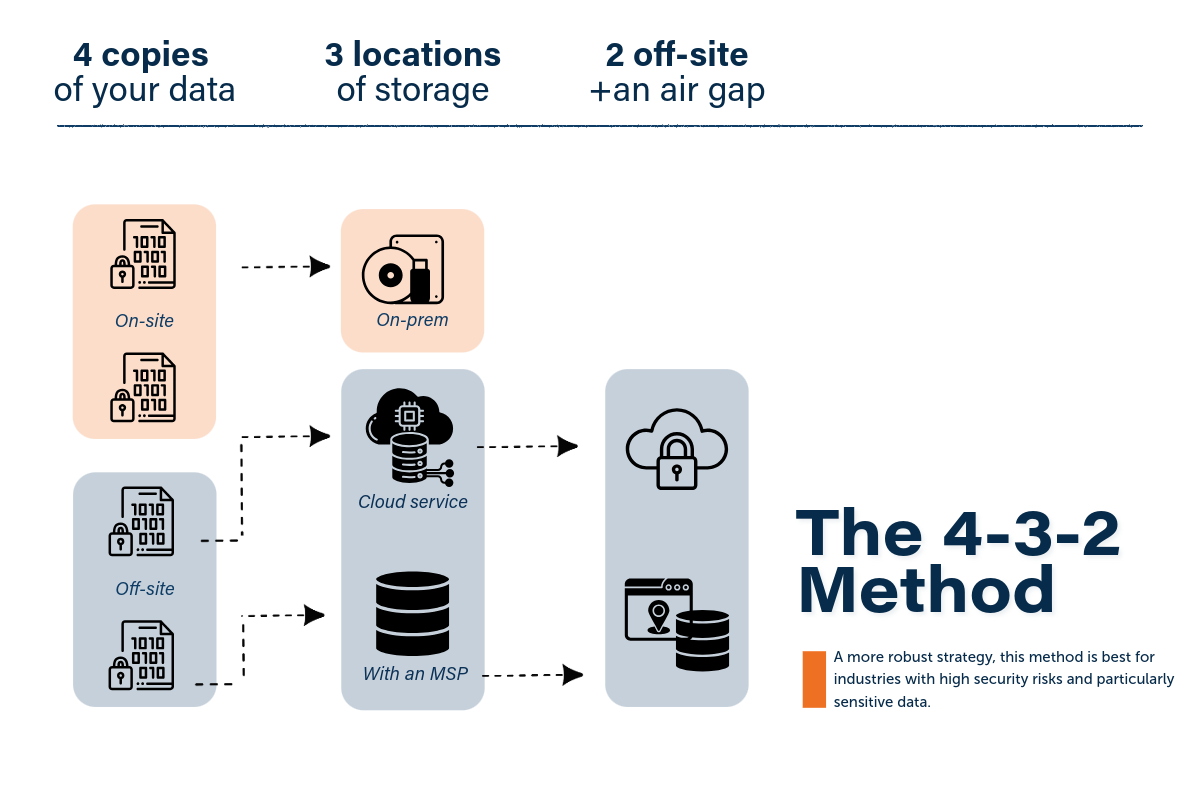
A Step Further: The 4-3-2 Rule
For organizations with greater security needs, such as those handling sensitive data or facing significant cyber risks, the 4-3-2 rule offers stronger safeguards in your data backup:
-
- Four copies of your data
- In three distinct locations (on-prem, with a managed service provider, and with a cloud service)
- With two off-site (one of which being air gapped)
With the 4-3-2 strategy, you’re not only practicing redundancy and immutability — you’re also protecting yourself from natural disasters and online threats to your network.
How High Point Networks Can Help with Data Backup and Protection
At High Point Networks, we’re committed to providing trusted IT solutions that help businesses, like yours, grow with confidence and support.
We don’t just offer technology. We’re here to solve real challenges with real people.
Our SMART backup solution / SMART Services listen to your business’s needs to ensure that we can help you eliminate unnecessary software and hardware and instead replace it with a streamlined, enterprise-level backup. Benefits include:
- Customizable solution sets (from backup to full blown DR)
- Flexible backup schedules and jobs
- Multiple options for immutable storage
- Comprehensive Veeam® licensing solutions
Ready for a smarter approach to data protection? Fill out the form below to learn how SMART solutions can transform your data protection strategy.
Get in Touch Today
Your business deserves nothing less than the best.
Get In Touch (Global)
Global contact us form
"*" indicates required fields

